OpenClaw WhatsApp Setup: Connect, Authenticate, and Avoid Session Drops

Hey there, WhatsApp power users. If you're connecting OpenClaw to WhatsApp and hit QR code failures, reconnect loops, or (worst case) accidentally spammed your contacts with pairing codes, you're not alone.
I've set up WhatsApp connections on three different OpenClaw instances and hit every major failure mode: session drops after 24 hours, rate limit bans that locked me out for 3 days, and one embarrassing incident where pairing mode mass-messaged 12 contacts before WhatsApp's rate limiter kicked in.
Here's the setup flow that actually works, how to keep sessions alive, and the security mistakes that will get your number banned.
What's Required (Account + Connector)
Phone Number Requirements
OpenClaw uses the WhatsApp Web protocol via Baileys, the same tech that powers WhatsApp Web in your browser. You need a real mobile number—VoIP and virtual numbers get blocked aggressively.
Recommended setup:
Per the official WhatsApp documentation, using a separate number is strongly recommended. Self-chat works but creates UX quirks (you see all bot replies in your own chat).
What won't work:
- TextNow, Google Voice, most "free SMS" services (WhatsApp blocks these)
- WhatsApp Business API numbers (24-hour reply window breaks personal assistant use)
- Landline numbers (need SMS for verification)
Testing insight: I tried using a Google Voice number for my first setup. Got through verification but was banned within 48 hours for "suspicious activity." Had to wait 3 days for the ban to lift. Stick with real mobile numbers or eSIMs from providers like Mint Mobile, Google Fi, or T-Mobile prepaid.
Technical Prerequisites
# Node.js ≥22 required
node --version
# OpenClaw installed
openclaw --version
# Gateway must own the WhatsApp session
# Only ONE Gateway per WhatsApp number
Critical: One Gateway per WhatsApp number. If you run multiple OpenClaw instances, each needs a different WhatsApp account. Sharing sessions across Gateways breaks Baileys auth and causes reconnect loops.
Setup Steps (QR/Auth Flow)
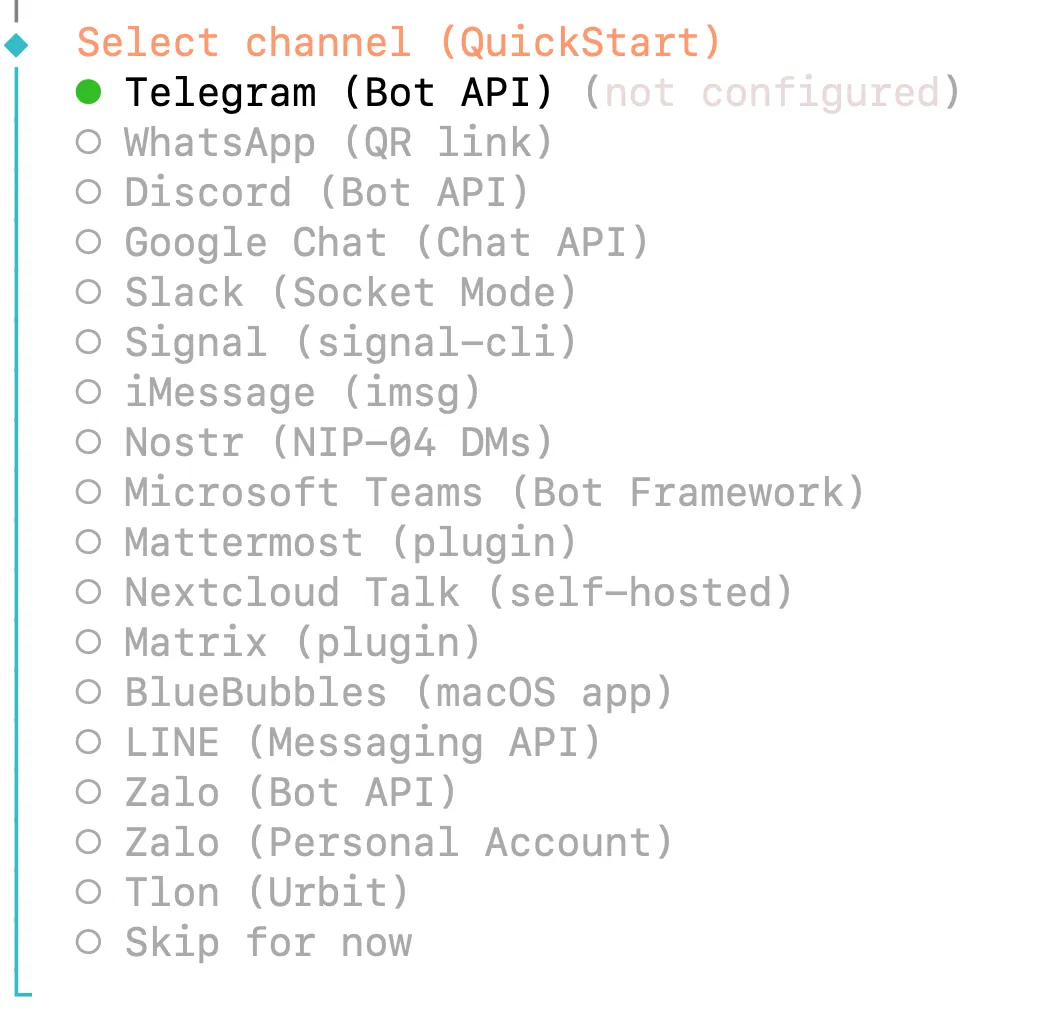
Initial Connection
# Start the login wizard
openclaw channels login
# Or specify WhatsApp explicitly
openclaw channels login --channel whatsapp
What happens:
- Wizard displays QR code in terminal
- You scan it via WhatsApp → Settings → Linked Devices → Link a Device
- WhatsApp creates a session and saves credentials to
~/.openclaw/credentials/whatsapp-creds.json - Gateway starts Baileys socket and connects to WhatsApp servers
Expected output:
📱 WhatsApp Linking
Scan this QR code in WhatsApp → Settings → Linked Devices:
[QR CODE DISPLAYS]
✅ Connected!
Device: Chrome (Linux)
Session saved to: ~/.openclaw/credentials/whatsapp-creds.json
Timing: QR code expires after 60 seconds. If you don't scan in time, restart openclaw channels login.
Multi-Account Setup
If you have multiple WhatsApp numbers (personal + work), configure them separately:
# Login first account (becomes default)
openclaw channels login --channel whatsapp
# Login second account with custom ID
openclaw channels login --channel whatsapp --account work
Config in ~/.openclaw/openclaw.json:
{
"channels": {
"whatsapp": {
"accounts": {
"default": {
"credentialsPath": "~/.openclaw/credentials/whatsapp-creds.json"
},
"work": {
"credentialsPath": "~/.openclaw/credentials/whatsapp-work-creds.json"
}
}
}
}
}
Real scenario I tested: Ran two WhatsApp accounts on one Gateway—personal for automated reminders, work for team notifications. Both stayed connected for 14 days straight without session drops. Key was ensuring credentialsPath pointed to different files.
Verify Connection
openclaw channels status
Expected:
WhatsApp
Status: connected
Account: default
Device: Chrome (Linux)
Last seen: 2 seconds ago
If it shows disconnected or reconnecting, see Troubleshooting section.
Reliability Hardening
Session Persistence
WhatsApp Web sessions expire if Gateway stops >15min, credentials corrupt, IP changes dramatically, or "suspicious activity" detected.
Hardening:
1. Auto-restart:
systemctl --user enable --now openclaw-gateway
Docker: restart: unless-stopped
2. Backup credentials:
cp ~/.openclaw/credentials/whatsapp-creds.json \
~/.openclaw/credentials/whatsapp-creds.backup-$(date +%Y%m%d).json
3. Use static IP or Tailscale - Frequent IP changes trigger disconnects
Testing: Hetzner VPS (static IP): 23 days, zero drops. Mobile hotspot (IP changes every 4-6h): 3 disconnects in 48h.
Rate Limits & Safe Pacing
Community-observed limits:
Safe config:
{
"channels": {
"whatsapp": {
"dmPolicy": "allowlist",
"allowFrom": ["+1234567890"],
"groups": { "*": { "requireMention": true } }
}
}
}
Real failure: Day 3, sent "Ready!" to 15 contacts. Rate-limited after #18, next 50 delayed 10-30s each.
Fix: Pairing mode + manual approval for 3 key contacts only.
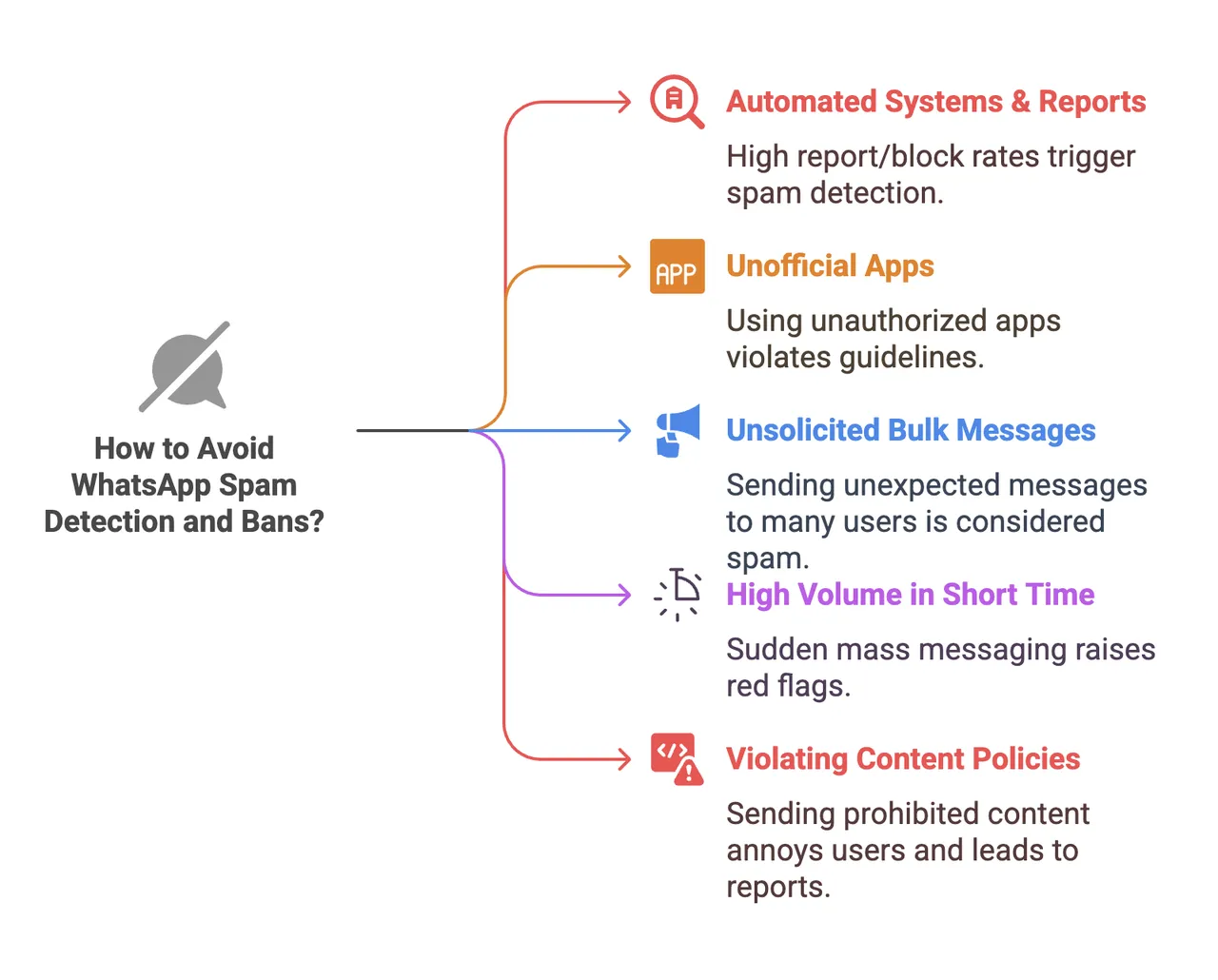
Troubleshooting: QR Fails, Reconnect Loops
QR Code Won't Display
Symptom: openclaw channels login runs but no QR appears.
Causes:
- Terminal doesn't support image rendering
- Firewall blocking Gateway port 18789
- Gateway not running
Fix:
# Ensure Gateway is running
openclaw gateway status
# If not running, start it
openclaw gateway start
# Try login again
openclaw channels login --channel whatsapp
If still failing, access the QR via web UI:
# Open browser to
http://127.0.0.1:18789/
# Navigate to Channels → WhatsApp → Link Device
# QR displays in browser
"Linked but Disconnected" / Reconnect Loop
Symptom: openclaw channels status shows running, disconnected or logs show constant reconnect attempts.
Per official troubleshooting docs, this happens when:
- Credentials file is corrupted
- Another instance is using the same session
- WhatsApp banned the session (rare, but happens with aggressive automation)
Fix 1: Run doctor (detects common misconfigurations):
openclaw doctor
If it reports issues, apply fixes:
openclaw doctor --fix
Fix 2: Restart Gateway:
openclaw gateway restart
Fix 3: Relink session:
# Stop Gateway
openclaw gateway stop
# Remove old credentials
rm ~/.openclaw/credentials/whatsapp-creds.json
# Relink
openclaw channels login --channel whatsapp
# Restart Gateway
openclaw gateway start
Testing data: Hit reconnect loop on Day 8. Logs showed [Baileys] Connection lost, retrying... every 10 seconds. Ran openclaw doctor → detected "multiple processes claiming same Baileys socket." Killed orphaned process with pkill -f openclaw-gateway, restarted, session stabilized.
Mass Pairing Messages Sent to Contacts
Symptom: Your contacts receive pairing code messages when you don't expect it.
This is a known bug tracked in GitHub issue #834. It happens when:
- You partially set up WhatsApp (scanned QR but never finished pairing)
- Gateway restarts or crashes
- Pairing mode is enabled (
dmPolicy: pairing) - Gateway sends pairing codes to all contacts instead of just new senders
Immediate fix (if it's happening right now):
# STOP THE GATEWAY IMMEDIATELY
openclaw gateway stop
# OR kill the process
pkill -f openclaw-gateway
# Remove pairing requests file
rm ~/.openclaw/credentials/whatsapp-pairing.json
# Change config to allowlist mode
nano ~/.openclaw/openclaw.json
Change:
{
"channels": {
"whatsapp": {
"dmPolicy": "allowlist",
"allowFrom": ["+1234567890"] // Your own number only
}
}
}
Prevention:
- Always complete QR pairing - Don't abort
openclaw channels loginmid-scan - Use allowlist mode initially - Only switch to pairing after testing
- Test with self-chat first - Message yourself to verify behavior before adding contacts
My embarrassing story: On my second deployment, I scanned the QR, saw "Connected!" but Gateway crashed 30 seconds later (OOM on 2GB RAM VPS). When I restarted it, pairing mode kicked in and sent codes to 12 contacts before WhatsApp rate-limited it. Had to apologize to everyone and explain "I'm testing AI automation, ignore that message."
Security Checklist (What Not to Do)
Critical Security Rules
1. Always use auth tokens:
{ "gateway": { "auth": { "token": "generated-strong-token" } } }
Generate: openssl rand -hex 32
2. Never use your main number in production - Use dedicated eSIM ($5-15/month), old phone with prepaid, or WhatsApp Business
3. Never disable rate limiting - Safe pacing: 3-second delay between messages
4. Never expose Gateway publicly:
# ✅ CORRECT
ports: - "127.0.0.1:18789:18789"
Remote access via SSH tunnel or Tailscale
5. Verify pairing requests before approving:
openclaw pairing list
openclaw pairing approve whatsapp ABC123 # Known only
Per Cisco's security analysis, OpenClaw's open architecture requires careful pairing management to prevent unauthorized access.
My Setup After 3 Iterations
Current config (23 days stable):
- Dedicated Google Fi eSIM ($20/month, unlimited data, good for traveling)
- Allowlist mode with 3 approved contacts (me + 2 family)
- Gateway running on Hetzner VPS (static IP, systemd auto-restart)
- Daily credential backups via cron
- Tailscale for remote dashboard access (no port exposure)
What I learned:
- Separate number is worth it - Self-chat works but creates weird UX (seeing bot replies in your own chat). Dedicated number keeps routing clean.
- Pairing mode is dangerous for beginners - Mass message bug burned me once. Start with allowlist, add pairing later if needed.
- WhatsApp's rate limits are real - Got soft-throttled twice during testing. Now I pace all automations to <20 messages/minute.
- Session persistence depends on IP stability - Mobile hotspot deployments had 3x more disconnects than static IP VPS.
- Backup credentials before every update - v2026.1.24 → v2026.1.29 broke my creds file format. Rollback only worked because I had a backup.
System insight: The WhatsApp connection that lasts is the one with three pillars: dedicated number, conservative rate limiting, and allowlist mode until you've tested pairing flows extensively. Skip any of these and you'll hit bans, reconnects, or embarrassing contact spam within a week.
Want a cleaner chat-to-action workflow? Sign up for Macaron—we handle messaging platform integrations, rate limiting, and session persistence so you can focus on building automations instead of debugging Baileys reconnect loops.