OpenClaw Telegram Bot Setup: Commands, Routing, and Multi-Agent Sessions
Hey automation builders — if you're wiring up OpenClaw to Telegram and wondering how routing actually works when messages start flying in from DMs, groups, and topics, stick around.
I spent the last two weeks running OpenClaw through Telegram in three different setups: personal DMs, team groups, and forum topics. Not demo scenarios. Real routing tests where I deliberately broke session isolation, flooded it with concurrent requests, and watched how the Gateway handled multi-account configs.
The question I kept coming back to: Can this actually maintain clean session boundaries when you're juggling multiple chats, or does it all collapse into one messy conversation thread?
Here's what I found, plus the exact config patterns that survived.
For context, OpenClaw (previously Moltbot and Clawdbot) gained over 100,000 GitHub stars in early 2026 as an open-source autonomous AI assistant. Created by Peter Steinberger, it connects messaging platforms like Telegram to AI agents running locally or on private servers.

Create a Telegram Bot (BotFather)
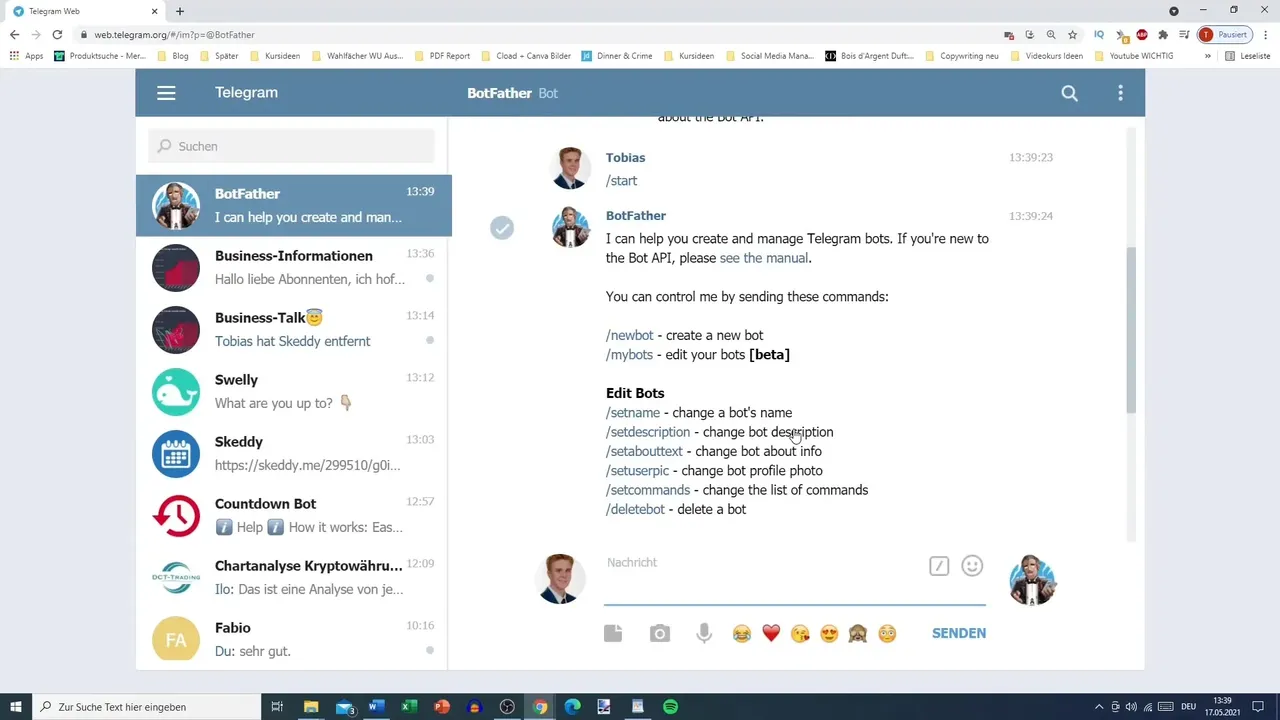
Every OpenClaw Telegram setup starts with @BotFather, Telegram's official bot creation interface. This hasn't changed since Telegram launched bots — it's still the only way to generate API tokens.
What you'll need:
- Active Telegram account (phone verification required)
- 3 minutes for initial setup
- Bot token stored somewhere secure (I use a password manager)
Step-by-step bot creation
- Open Telegram and search for @BotFather
- Verified account has a blue checkmark
- Send
/startto see available commands
- Create new bot with
/newbot- Bot name: What users see in conversations (can include spaces)
- Username: Must end with
bot(e.g.,YourProjectBot) - Username must be globally unique across Telegram
- Save your API token immediately
- Format:
123456789:ABCdefGHIjklMNOpqrsTUVwxyz - Treat this like a password — anyone with this token controls your bot
- If compromised, use
/revokein BotFather to generate a new one
- Format:
Critical BotFather settings (optional but recommended):
/setjoingroups → Allow/deny adding bot to groups
/setprivacy → OFF = bot sees all group messages
ON = bot only sees mentions and commands
I learned this the hard way: if you set privacy to ON and wonder why your bot ignores group messages, that's why. OpenClaw's routing expects full message access by default.
Connect Token + Verify Updates
Getting the token into OpenClaw is where most setup guides stop — but that's where real testing should start.
Basic connection config
OpenClaw supports two token input methods:
Environment variable (quick testing):
export TELEGRAM_BOT_TOKEN="your_token_here"
openclaw gateway
Config file (production approach):
{
"channels": {
"telegram": {
"enabled": true,
"botToken": "123456789:ABCdefGHIjklMNOpqrsTUVwxyz",
"dmPolicy": "pairing"
}
}
}
Verification test sequence
Here's the sequence I run every time to confirm the Gateway actually sees Telegram updates:
- Start Gateway with logging:
openclaw gateway --log-level debug
- Send
/startto your bot in Telegram- Should trigger pairing flow if
dmPolicy: "pairing" - Check terminal for incoming update logs
- Should trigger pairing flow if
- Monitor update stream:
openclaw logs --follow
Common failure point: Bot token typo. If you see 401 Unauthorized in logs, regenerate the token in BotFather and update your config. Don't waste an hour troubleshooting like I did.
Security note: For production deployments, consider using DigitalOcean's hardened OpenClaw image which includes firewall rules, container isolation, and non-root execution by default.
Command Design That Scales
OpenClaw's command system is where routing logic starts to matter. The Gateway recognizes slash commands across all channels, but Telegram adds its own command autocomplete layer.
The official OpenClaw repository documents the full command set, but after real-world testing, only a handful prove essential.
Core command patterns
These are the commands I actually use in production setups (not the full list — just what survives real usage):
Important: /activation always only affects the current session. To persist it, add it to your config's requireMention settings.
Setting up custom commands in BotFather
This is what makes your bot feel native in Telegram:
- In BotFather:
/mybots→ Select your bot →Edit Commands - Send command list (one per line):
new - Start fresh sessionstatus - Check session statehelp - Show all commands
- These appear in Telegram's
/autocomplete menu
Reality check: I initially set up 15 commands. After two weeks, I only use 4. Start minimal.
For deeper understanding of Telegram's bot architecture, see the official Telegram Bot tutorial which covers the Bot API fundamentals.
Routing by Chat/User/Topic
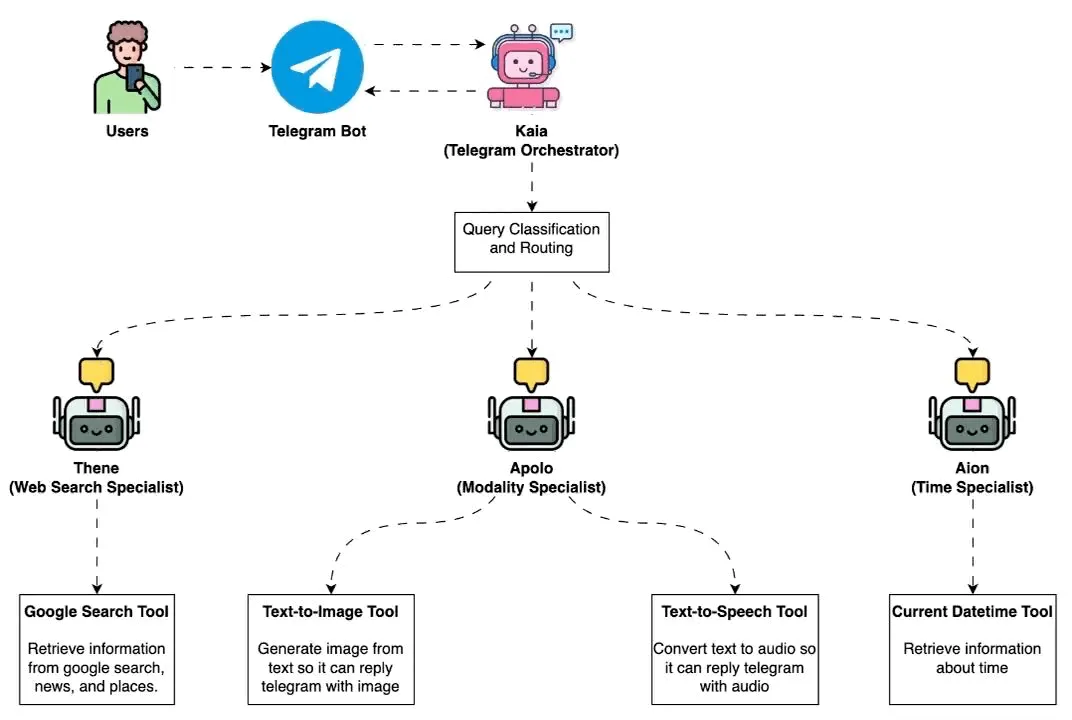
This is where OpenClaw's session architecture either makes sense or falls apart. Session keys determine whether conversations stay isolated or bleed together.
Session key structure
OpenClaw generates session keys using this pattern:
agent:<agentId>:telegram:<chatType>:<chatId>[:topic:<topicId>]
Breakdown:
- DMs: All messages from one user → shared
mainsession - Groups: Each group → isolated session (
telegram:group:<chatId>) - Forum topics: Each topic → separate session (
:topic:<threadId>suffix)
Multi-account routing config
Here's a real config I ran for testing three separate Telegram bots routing to different agents:
{
"channels": {
"telegram": {
"accounts": [
{
"name": "personal",
"botToken": "token1...",
"routing": { "agent": "main" }
},
{
"name": "work",
"botToken": "token2...",
"routing": { "agent": "work-agent" }
},
{
"name": "testing",
"botToken": "token3...",
"routing": { "agent": "sandbox" }
}
]
}
}
}
Each account routes to a separate agent workspace with independent memory and tools. No cross-contamination.
Group routing with mention controls
Default behavior: groups require @mention to trigger responses. Override per-group:
{
"channels": {
"telegram": {
"groups": {
"*": { "requireMention": true },
"-1001234567890": {
"requireMention": false
}
}
}
}
}
Group ID discovery: Add bot to group, send a message, check openclaw logs --follow for the chat.id value (always negative for groups).
Forum topic isolation
Telegram forums add message_thread_id to messages. OpenClaw appends :topic:<threadId> to session keys automatically.
Critical edge case I hit: Topic ID 1 (general topic) requires special handling. OpenClaw omits message_thread_id when sending to topic 1 because Telegram rejects it.
Config example for per-topic system prompts:
{
"telegram": {
"groups": {
"-1003595003457": {
"requireMention": false,
"topics": {
"14": {
"requireMention": false,
"systemPrompt": "You are a coding assistant."
},
"27": {
"systemPrompt": "You focus on deployment issues."
}
}
}
}
}
}
Each topic maintains isolated conversation history.
Debugging Missed Messages
When messages disappear into the void, it's usually one of these three culprits.
Diagnostic checklist
- Check BotFather privacy settings
/mybots → Your Bot → Bot Settings → Group Privacy → OFF
- If ON, bot only sees mentions — not regular messages.
- Verify group whitelist
openclaw logs --follow | grep "skipping group message"
- If
channels.telegram.groupsis defined, unlisted groups are ignored. - Confirm bot membership
- Bot must be added as a member (not just admin with no read access)
- Test: send a message, check if bot's "last seen" timestamp updates
- Review Gateway logs
openclaw logs --level debug --filter telegram
Common routing failures
Session hygiene checks
I run this sequence weekly to catch routing drift:
# List active sessions
openclaw sessions list
# Check specific session state
openclaw sessions show <sessionKey>
# Force session cleanup (last resort)
openclaw sessions prune --older-than 7d
When sessions leak: If you see context bleeding between chats, it's usually a config error where multiple chats map to the same session key. Review channels.telegram.accounts[].routing.agent settings.
What Actually Worked Long-Term
After two weeks of daily use across three different Telegram setups, here's what survived:
Stable config pattern
{
"channels": {
"telegram": {
"enabled": true,
"botToken": "env:TELEGRAM_BOT_TOKEN",
"dmPolicy": "pairing",
"groups": {
"*": { "requireMention": true }
}
}
}
}
Why this works:
- DM pairing prevents unauthorized access
- Wildcard group policy with mention requirement = safe defaults
- Token from env var = easier rotation without touching config
What didn't scale
- Custom commands beyond
/new,/status,/help— Users forget them - Per-topic system prompts — Maintenance burden grows fast
- Multiple accounts without clear routing rules — Session chaos
Boundary conditions
OpenClaw Telegram routing is solid for:
- Personal DM automation (single user)
- Small team groups (< 20 active members)
- Forum topics with distinct purposes
It gets messy when:
- You're managing 10+ groups without config discipline
- Users expect instant responses (add queue monitoring)
- Session state matters across Gateway restarts (implement persistence checks)
Security reminder: As noted in security analysis, OpenClaw stores session transcripts and credentials locally. Treat your ~/.openclaw directory as sensitive — use encrypted drives and restrict file permissions.
If OpenClaw + Telegram gets you where you need to go, run with it. Just keep session keys clean and know which groups get which agent.
At Macaron, we handle the same routing challenges automatically — session isolation across platforms, no manual config patching when you add channels. If you want to test multi-platform routing without rebuilding configs every time you scale, try it with a real workflow and see how it handles your setup.